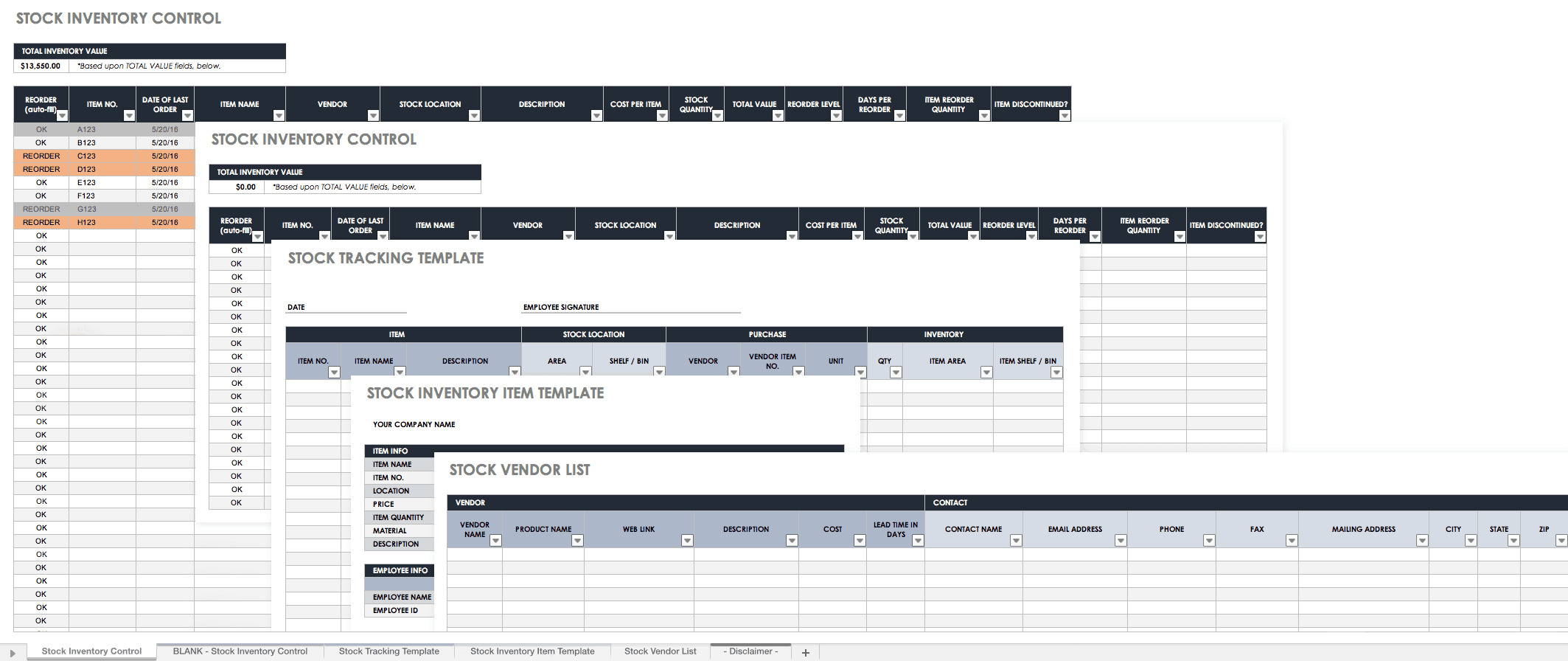
Microsoft Content Management Server Templates
Template format
The Page Content control comes from Microsoft Content Management Server, it’s different from the web part and you cannot easily edit it now (Maybe next version). However, you can change the layout of the page in SharePoint Designer 2007, but you cannot modify the content of the page. The default page path is pagesdefault.aspx. The release of Microsoft Content Management Server (MCMS) Service Pack 2 opens up the world of ASP.NET 2.0 to MCMS developers. Written by the masters of MCMS, this book shows you how to use the new features of ASP.NET 2.0 that everyone is talking about in your MCMS development. Microsoft Content Management Server: Configuring Templates to Allow Postings to Return Accurate Last Modified Time 4/5/2012 5:51:49 PM - Video: How to create your first Swimlane Diagram or Cross-Functional Flowchart Diagram by using Microsoft Visio 2010. Preferred and charter members. To help accelerate customer success with Microsoft 365 Content Services, powered by Microsoft 365, Project Cortex, SharePoint, and SharePoint Syntex, we launched the Microsoft 365 Content Services Partner Program to support our partners delivering solutions that make the transformation of your content management approach practical and attainable.
To create a Microsoft.ApiManagement/service resource, add the following JSON to the resources section of your template.
Property values
The following tables describe the values you need to set in the schema.
Microsoft.ApiManagement/service object
| Name | Type | Required | Value |
|---|---|---|---|
| name | string | Yes | The name of the API Management service. |
| type | enum | Yes | Microsoft.ApiManagement/service |
| apiVersion | enum | Yes | 2020-06-01-preview |
| tags | object | No | Resource tags. |
| properties | object | Yes | Properties of the API Management service. - ApiManagementServiceProperties object |
| sku | object | Yes | SKU properties of the API Management service. - ApiManagementServiceSkuProperties object |
| identity | object | No | Managed service identity of the Api Management service. - ApiManagementServiceIdentity object |
| location | string | Yes | Resource location. |
| zones | array | No | A list of availability zones denoting where the resource needs to come from. - string |
ApiManagementServiceProperties object
| Name | Type | Required | Value |
|---|---|---|---|
| notificationSenderEmail | string | No | Email address from which the notification will be sent. |
| hostnameConfigurations | array | No | Custom hostname configuration of the API Management service. - HostnameConfiguration object |
| virtualNetworkConfiguration | object | No | Virtual network configuration of the API Management service. - VirtualNetworkConfiguration object |
| additionalLocations | array | No | Additional datacenter locations of the API Management service. - AdditionalLocation object |
| customProperties | object | No | Custom properties of the API Management service. Setting Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Ciphers.TripleDes168 will disable the cipher TLS_RSA_WITH_3DES_EDE_CBC_SHA for all TLS(1.0, 1.1 and 1.2).Setting Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Protocols.Tls11 can be used to disable just TLS 1.1.Setting Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Protocols.Tls10 can be used to disable TLS 1.0 on an API Management service.Setting Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Backend.Protocols.Tls11 can be used to disable just TLS 1.1 for communications with backends.Setting Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Backend.Protocols.Tls10 can be used to disable TLS 1.0 for communications with backends.Setting Microsoft.WindowsAzure.ApiManagement.Gateway.Protocols.Server.Http2 can be used to enable HTTP2 protocol on an API Management service.Not specifying any of these properties on PATCH operation will reset omitted properties' values to their defaults. For all the settings except Http2 the default value is True if the service was created on or before April 1st 2018 and False otherwise. Http2 setting's default value is False.You can disable any of next ciphers by using settings Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Ciphers.[cipher_name]: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_256_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA. For example, Microsoft.WindowsAzure.ApiManagement.Gateway.Security.Ciphers.TLS_RSA_WITH_AES_128_CBC_SHA256:false. The default value is true for them. Note: next ciphers can't be disabled since they are required by Azure CloudService internal components: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384 |
| certificates | array | No | List of Certificates that need to be installed in the API Management service. Max supported certificates that can be installed is 10. - CertificateConfiguration object |
| enableClientCertificate | boolean | No | Property only meant to be used for Consumption SKU Service. This enforces a client certificate to be presented on each request to the gateway. This also enables the ability to authenticate the certificate in the policy on the gateway. |
| disableGateway | boolean | No | Property only valid for an Api Management service deployed in multiple locations. This can be used to disable the gateway in master region. |
| virtualNetworkType | enum | No | The type of VPN in which API Management service needs to be configured in. None (Default Value) means the API Management service is not part of any Virtual Network, External means the API Management deployment is set up inside a Virtual Network having an Internet Facing Endpoint, and Internal means that API Management deployment is setup inside a Virtual Network having an Intranet Facing Endpoint only. - None, External, Internal |
| apiVersionConstraint | object | No | Control Plane Apis version constraint for the API Management service. - ApiVersionConstraint object |
| restore | boolean | No | Undelete Api Management Service if it was previously soft-deleted. If this flag is specified and set to True all other properties will be ignored. |
| publisherEmail | string | Yes | Publisher email. |
| publisherName | string | Yes | Publisher name. |
ApiManagementServiceSkuProperties object
| Name | Type | Required | Value |
|---|---|---|---|
| name | enum | Yes | Name of the Sku. - Developer, Standard, Premium, Basic, Consumption, Isolated |
| capacity | integer | Yes | Capacity of the SKU (number of deployed units of the SKU). For Consumption SKU capacity must be specified as 0. |
ApiManagementServiceIdentity object
| Name | Type | Required | Value |
|---|---|---|---|
| type | enum | Yes | The type of identity used for the resource. The type 'SystemAssigned, UserAssigned' includes both an implicitly created identity and a set of user assigned identities. The type 'None' will remove any identities from the service. - SystemAssigned, UserAssigned, SystemAssigned, UserAssigned, None |
| userAssignedIdentities | object | No | The list of user identities associated with the resource. The user identity dictionary key references will be ARM resource ids in the form: '/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.ManagedIdentity/userAssignedIdentities/{identityName}'. |
HostnameConfiguration object
| Name | Type | Required | Value |
|---|---|---|---|
| type | enum | Yes | Hostname type. - Proxy, Portal, Management, Scm, DeveloperPortal |
| hostName | string | Yes | Hostname to configure on the Api Management service. |
| keyVaultId | string | No | Url to the KeyVault Secret containing the Ssl Certificate. If absolute Url containing version is provided, auto-update of ssl certificate will not work. This requires Api Management service to be configured with MSI. The secret should be of type application/x-pkcs12 |
| identityClientId | string | No | System or User Assigned Managed identity clientId as generated by Azure AD, which has GET access to the keyVault containing the SSL certificate. |
| encodedCertificate | string | No | Base64 Encoded certificate. |
| certificatePassword | string | No | Certificate Password. |
| defaultSslBinding | boolean | No | Specify true to setup the certificate associated with this Hostname as the Default SSL Certificate. If a client does not send the SNI header, then this will be the certificate that will be challenged. The property is useful if a service has multiple custom hostname enabled and it needs to decide on the default ssl certificate. The setting only applied to Proxy Hostname Type. |
| negotiateClientCertificate | boolean | No | Specify true to always negotiate client certificate on the hostname. Default Value is false. |
| certificate | object | No | Certificate information. - CertificateInformation object |
VirtualNetworkConfiguration object
| Name | Type | Required | Value |
|---|---|---|---|
| subnetResourceId | string | No | The full resource ID of a subnet in a virtual network to deploy the API Management service in. |
Microsoft Content Management Systems
AdditionalLocation object
| Name | Type | Required | Value |
|---|---|---|---|
| location | string | Yes | The location name of the additional region among Azure Data center regions. |
| sku | object | Yes | SKU properties of the API Management service. - ApiManagementServiceSkuProperties object |
| zones | array | No | A list of availability zones denoting where the resource needs to come from. - string |
| virtualNetworkConfiguration | object | No | Virtual network configuration for the location. - VirtualNetworkConfiguration object |
| disableGateway | boolean | No | Property only valid for an Api Management service deployed in multiple locations. This can be used to disable the gateway in this additional location. |
CertificateConfiguration object
| Name | Type | Required | Value |
|---|---|---|---|
| encodedCertificate | string | No | Base64 Encoded certificate. |
| certificatePassword | string | No | Certificate Password. |
| storeName | enum | Yes | The System.Security.Cryptography.x509certificates.StoreName certificate store location. Only Root and CertificateAuthority are valid locations. - CertificateAuthority or Root |
| certificate | object | No | Certificate information. - CertificateInformation object |

ApiVersionConstraint object

| Name | Type | Required | Value |
|---|---|---|---|
| minApiVersion | string | No | Limit control plane API calls to API Management service with version equal to or newer than this value. |
CertificateInformation object
| Name | Type | Required | Value |
|---|---|---|---|
| expiry | string | Yes | Expiration date of the certificate. The date conforms to the following format: yyyy-MM-ddTHH:mm:ssZ as specified by the ISO 8601 standard. |
| thumbprint | string | Yes | Thumbprint of the certificate. |
| subject | string | Yes | Subject of the certificate. |
Quickstart templates
The following quickstart templates deploy this resource type.
| Template | Description |
|---|---|
| Create an API Management instance having MSI Identity | This template creates a developer instance of Azure API Management having an MSI Identity |
| Create an API Management service with SSL from KeyVault | This template deploys an API Management service configured with User Assigned Identity. It uses this identity to fetch SSL certificate from KeyVault and keeps it updated by checking every 4 hours. |
| Create an API Management instance using a template | This template creates a developer instance of Azure API Management |
| Create an API Management instance and all sub resources using template | This template demonstrates how to create a API Management service and configure sub-entities |
| Create an API Management service in External Virtual Network | This template demonstrates how to create a instance of Azure API Management within your virtual network's subnet in External mode and configure NSG on the subnet as per recommendation. |
| Create an API Management instance in Premium tier with custom hostnames for proxy and portal | This template demonstrates how to create a instance of Azure API Management with custom hostname for portal and multiple custom hostnames for proxy |
| Create an API Management service in Internal Virtual network | This template demonstrates how to create a instance of Azure API Management within your virtual network's subnet in Internal Virtual Network mode and configure NSG on the subnet as per recommendation. |
| Create a multi-region Premium tier API Management service | This template demonstrates how to create API Management service with additional locations. The primary location is the same as location of the resource group. For Additional locations, the template shows NorthCentralUs and East US2. The primary location should be different from additional locations |
| Create API Management with custom proxy ssl using KeyVault. | This template demonstrates how to Create a instance of Azure API Management and configure custom hostname for proxy with ssl certificate from keyvault. |
| Create and monitor API Management instance with Operations Management Suite (OMS) - Log Analytics | This template creates an instance of Azure API Management service and OMS workspace and sets up monitoring for your API Management service with Operations Management Suite - Log Analytics |
| Create Azure Front Door in front of Azure API Management | This sample demonstrates how to use Azure Front Door as a global load balancer in front of Azure API Management. |
Applies to: Windows Server (Semi-Annual Channel), Windows Server 2016
You can use this procedure to configure the certificate template that Active Directory® Certificate Services (AD CS) uses as the basis for server certificates that are enrolled to servers on your network.
While configuring this template, you can specify the servers by Active Directory group that should automatically receive a server certificate from AD CS.
The procedure below includes instructions for configuring the template to issue certificates to all of the following server types:
- Servers that are running the Remote Access service, including RAS Gateway servers, that are members of the RAS and IAS Servers group.
- Servers that are running the Network Policy Server (NPS) service that are members of the RAS and IAS Servers group.
Membership in both the Enterprise Admins and the root domain's Domain Admins group is the minimum required to complete this procedure.
To configure the certificate template
Microsoft Content Management Tools
On CA1, in Server Manager, click Tools, and then click Certification Authority. The Certification Authority Microsoft Management Console (MMC) opens.
In the MMC, double-click the CA name, right-click Certificate Templates, and then click Manage.
The Certificate Templates console opens. All of the certificate templates are displayed in the details pane.
In the details pane, click the RAS and IAS Server template.
Click the Action menu, and then click Duplicate Template. The template Properties dialog box opens.
Click the Security tab.
On the Security tab, in Group or user names, click RAS and IAS servers.
In Permissions for RAS and IAS servers, under Allow, ensure that Enroll is selected, and then select the Autoenroll check box. Click OK, and close the Certificate Templates MMC.
In the Certification Authority MMC, click Certificate Templates. On the Action menu, point to New, and then click Certificate Template to Issue. The Enable Certificate Templates dialog box opens.
In Enable Certificate Templates, click the name of the certificate template that you just configured, and then click OK. For example, if you did not change the default certificate template name, click Copy of RAS and IAS Server, and then click OK.
